Security Monitoring Radar: The Ultimate Guide to Unblinking, All-Weather Perimeter Protection
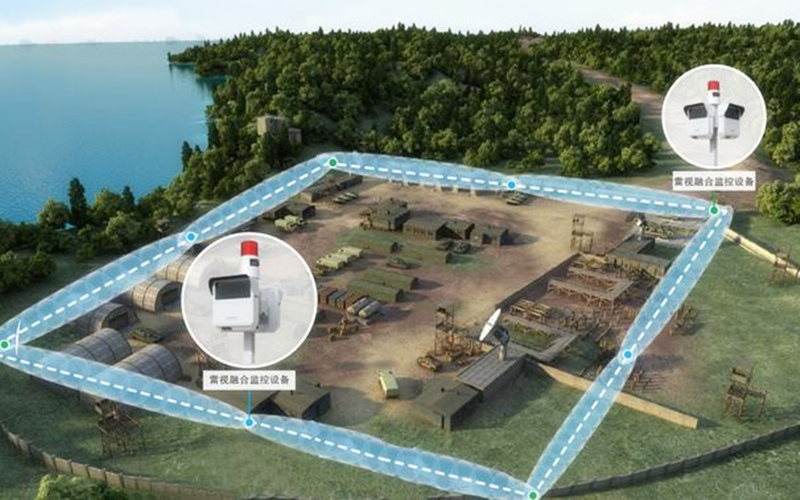
Introduction: The Critical Evolution of Security Monitoring
In an era of escalating physical security threats, organizations demand solutions that transcend the limitations of human guards and traditional cameras. Security monitoring radar has emerged as the cornerstone of modern, proactive protection strategies. Unlike optical systems hampered by darkness, fog, or glare, radar provides persistent, all-weather, 24/7 surveillance capable of detecting, classifying, and tracking potential intrusions with remarkable accuracy across vast, complex terrains. This comprehensive guide delves deep into the technology, applications, benefits, and future of radar-based security monitoring, empowering you to make informed decisions for safeguarding critical assets.
Part 1: Understanding the Core Technology – How Radar Sees the Unseen
-
1.1 Fundamental Principles: Explaining electromagnetic wave propagation, reflection (backscatter), Doppler effect (detecting movement), and time-of-flight calculations.
-
1.2 Key Components Demystified:
-
Transmitter: Generating high-frequency radio waves (commonly X-band (9-10 GHz), K-band (24-26 GHz), W-band (76-81 GHz)).
-
Antenna: Directing energy and receiving echoes (Phased Array, Mechanical Scanning, MIMO configurations).
-
Receiver: Amplifying and processing extremely weak return signals.
-
Signal Processor: The “brain” – applying complex algorithms for clutter rejection, target detection, classification, and tracking (Kalman filters, CFAR).
-
-
1.3 Waveform Types & Their Advantages:
-
FMCW (Frequency Modulated Continuous Wave): Dominant in security. Offers range, velocity measurement, lower power, and excellent resolution. Detailed explanation of chirp signals.
-
Pulse Doppler: Used in longer-range applications. Pulse characteristics and velocity detection via Doppler shift.
-
UWB (Ultra-Wideband): Emerging for high resolution and material penetration.
-
-
1.4 Critical Performance Metrics:
-
Range & Coverage: Maximum detection distance and angular field of view (FoV).
-
Resolution: Ability to distinguish between closely spaced targets (Range Resolution, Angular Resolution).
-
Accuracy: Precision in determining target location and speed.
-
Update Rate: How frequently the radar scans its environment.
-
Probability of Detection (Pd) vs. False Alarm Rate (FAR): The fundamental trade-off optimized by advanced processing.
-
Multi-Target Tracking (MTT) Capacity: Number of simultaneous targets tracked.
-
Part 2: Why Radar is Revolutionizing Security Monitoring
-
2.1 Unmatched Environmental Resilience:
-
All-Weather Operation: Performance unaffected by rain, snow, fog, smoke, dust, or sandstorms.
-
24/7 Daylight & Darkness Capability: No reliance on visible light or thermal contrast.
-
Penetration Capabilities: Seeing through light foliage, thin walls, or non-metallic fences in specific configurations.
-
-
2.2 Superior Detection Performance:
-
Long-Range Coverage: Monitoring perimeters spanning kilometers from a single sensor.
-
High Sensitivity: Detecting crawling personnel, small vehicles, or drones at significant distances.
-
Velocity Filtering: Discriminating genuine threats from background clutter (wind-blown vegetation, animals) using Doppler.
-
Reduced Nuisance Alarms: Advanced algorithms significantly lower FAR compared to basic PIR or seismic sensors.
-
-
2.3 Enhanced Situational Awareness:
-
Precise Target Localization: Providing real-time X/Y (or X/Y/Z) coordinates on a map.
-
Continuous Tracking: Monitoring target paths, speed, and direction.
-
Classification Capabilities: Differentiating between humans, vehicles, animals, and drones (increasingly AI-driven).
-
-
2.4 Cost-Effectiveness & Scalability:
-
Wide Area Coverage: Fewer sensors needed compared to cameras or point sensors for large perimeters.
-
Reduced Guarding Costs: Automating surveillance of large, remote, or hazardous areas.
-
Flexible Deployment: Adaptable to diverse terrains (flat, hilly, coastal, urban).
-
Part 3: Diverse Applications of Security Monitoring Radar
-
3.1 Critical Infrastructure Protection (CIP):
-
Power Plants (Nuclear, Fossil Fuel, Renewable)
-
Substations & Transmission Corridors
-
Oil & Gas Facilities (Refineries, Pipelines, Offshore Platforms)
-
Water Treatment Plants & Reservoirs
-
Airports & Seaports
-
-
3.2 Commercial & Industrial Security:
-
Manufacturing Plants & Warehouses
-
Logistics Hubs & Distribution Centers
-
Data Centers
-
Mining Operations
-
Corporate Campuses
-
-
3.3 Border & Perimeter Security:
-
National Borders
-
Military Bases & Depots
-
Prisons & Correctional Facilities
-
Sensitive Government Sites
-
-
3.4 Urban & Public Space Security:
-
Smart City Perimeters (Critical Buildings)
-
Stadiums & Large Event Venues
-
Mass Transit Facilities
-
Parks & Sensitive Urban Zones
-
-
3.5 High-Value Residential & Estate Security
-
3.6 Counter-Drone (C-UAS) Applications: Detection and tracking of unauthorized drones.
Part 4: Types of Security Radars & Selection Criteria
-
4.1 Short-Range Perimeter Radars (< 500m):
-
Focus: High resolution for fence lines, entry points, critical assets.
-
Technology: Often higher frequency (K-band, W-band), FMCW.
-
Use Case: Detailed monitoring of sensitive inner zones.
-
-
4.2 Medium-Range Radars (500m – 3km):
-
Focus: Balancing coverage and resolution for typical facility perimeters.
-
Technology: X-band, K-band FMCW prevalent.
-
Use Case: Most common for industrial sites, campuses.
-
-
4.3 Long-Range Radars (3km – 15km+):
-
Focus: Wide area surveillance, early warning.
-
Technology: Often lower frequency (S-band, C-band), Pulse Doppler or FMCW.
-
Use Case: Borders, large airports, coastal monitoring, vast critical infrastructure.
-
-
4.4 Ground Surveillance Radars (GSR): Specifically optimized for detecting crawling/creeping personnel and ground vehicles in cluttered terrain.
-
4.5 3D Radars: Adding elevation data for complex terrain, urban canyons, or drone detection/tracking.
-
4.6 Selecting the Right Radar:
-
Defining Coverage Requirements (Range, FoV, Terrain Complexity)
-
Identifying Primary Threats (Human, Vehicle, Drone, Watercraft)
-
Environmental Conditions (Extreme Weather, EMI Sources)
-
Integration Needs (VMS, PSIM, Access Control, Camera Systems)
-
Power & Infrastructure Constraints
-
Budget & Total Cost of Ownership (TCO)
-
Part 5: Integration – The Power of Sensor Fusion
-
5.1 The “Force Multiplier” Effect: Why radar + cameras + other sensors is essential.
-
5.2 Radar-Guided PTZ Cameras:
-
Radar detects and locates target.
-
Automatically slews PTZ camera to zoom in on precise location.
-
Provides visual verification, identification, and evidence.
-
Overcomes camera limitations (blind spots, poor conditions).
-
-
5.3 Integration with VMS/PSIM:
-
Radar data as an input layer on the security operations map.
-
Automated alarm generation and operator guidance.
-
Correlation with access control events or other sensor alarms.
-
-
5.4 Fusion with Thermal & EO/IR Cameras: Leveraging strengths of each technology.
-
5.5 Integrating with Access Control & Intrusion Detection Systems (IDS): Creating layered defense.
-
5.6 Communication Protocols: Importance of open standards (ONVIF Profile D for radar, others).
Part 6: Advanced Features & AI in Modern Security Radars
-
6.1 AI-Powered Target Classification: Moving beyond basic size/speed:
-
Human vs. Vehicle vs. Animal vs. Drone discrimination.
-
Distinguishing between personnel walking, running, crawling.
-
Identifying specific vehicle types.
-
-
6.2 Behavioral Analytics:
-
Detecting loitering, perimeter probing, abandoned objects.
-
Identifying movement patterns indicative of hostile intent.
-
Defining virtual “tripwires” and directional zones.
-
-
6.3 Adaptive Clutter Filtering: AI continuously learning and adapting to the environment to minimize false alarms (e.g., changing vegetation, weather patterns).
-
6.4 Automated Threat Assessment: Prioritizing alerts based on classification, behavior, and proximity to critical assets.
-
6.5 Multi-Radar Networking & Fusion: Seamlessly combining data from multiple radars for extended coverage or overlapping perspectives.
Part 7: Overcoming Challenges in Radar Deployment
-
7.1 Site Assessment & Planning:
-
Comprehensive RF survey (identifying interference sources).
-
Detailed terrain mapping and modeling.
-
Optimal sensor placement (height, tilt, orientation).
-
Line-of-Sight (LoS) vs. Non-Line-of-Sight (NLoS) considerations.
-
-
7.2 Mitigating Environmental Clutter:
-
Techniques for dealing with heavy vegetation, moving water, traffic corridors.
-
Configuration of exclusion zones and sensitivity settings.
-
-
7.3 Electromagnetic Interference (EMI):
-
Identifying potential sources (communications towers, industrial machinery).
-
Frequency selection and filtering strategies.
-
Regulatory compliance (FCC, CE, etc.).
-
-
7.4 Installation & Calibration: Importance of precise mounting and thorough calibration for accurate performance.
-
7.5 Cybersecurity: Securing radar data transmission and preventing system hacking (encryption, secure protocols, network segmentation).
Part 8: Future Trends in Security Monitoring Radar
-
8.1 Higher Frequencies & Wider Bandwidths: Enabling millimeter-wave (mmWave) radar for incredible resolution and small target detection (e.g., W-band).
-
8.2 Miniaturization & Cost Reduction: Making radar technology accessible for smaller sites and new applications.
-
8.3 Advanced MIMO (Multiple Input Multiple Output) Architectures: Improving resolution and angular accuracy without physically large antennas.
-
8.4 Deep Learning Integration: More sophisticated and adaptable AI for classification, behavior prediction, and anomaly detection.
-
8.5 Cognitive Radar: Systems that dynamically adapt waveforms and processing based on the real-time environment and threat profile.
-
8.6 Integration with 5G/IoT: Leveraging high-bandwidth, low-latency networks for distributed sensor networks and cloud analytics.
-
8.7 Quantum Radar (Emerging): Potential for unprecedented sensitivity and stealth detection capabilities (long-term horizon).
Part 9: Implementing a Radar-Based Security Monitoring System
-
9.1 Defining Security Objectives & Requirements: Clear goals drive technology selection.
-
9.2 Conducting a Thorough Risk Assessment: Identifying vulnerabilities and critical zones.
-
9.3 Partnering with Experienced Integrators: The crucial role of system design and deployment expertise.
-
9.4 Phased Deployment & Testing: Start with critical areas, validate performance, then expand.
-
9.5 Operator Training & Procedures: Ensuring personnel understand the system and can respond effectively to alerts.
-
9.6 Ongoing Maintenance & Optimization: Regular checks, software updates, and performance tuning.
Conclusion: The Indispensable Role of Radar in Modern Security
Security monitoring radar is no longer a niche technology but a fundamental component of a robust, proactive physical security strategy. Its unique ability to provide persistent, all-weather detection and tracking across vast areas, coupled with increasingly sophisticated AI-powered analytics, offers a level of situational awareness and early warning that is simply unattainable with traditional methods alone. As threats evolve and technology advances, radar will continue to be at the forefront, enabling security professionals to protect people, assets, and infrastructure more effectively and efficiently than ever before. Investing in a well-designed, integrated radar-based security monitoring system is an investment in resilience, operational continuity, and peace of mind.
